Hello!
 When employees worked on-site at the office, things seemed simple in many aspects, including security-wise.
When employees worked on-site at the office, things seemed simple in many aspects, including security-wise.
The comprehensive in-house cybersecurity infrastructure suffices to protect everyone and their respective data.
However, with the pandemic still looming over our heads, employers have no choice but to embrace remote work long-term.
This paradigm shift requires transferring the on-site cybersecurity model to the locations where their remote teams are working. While many are resistant to doing so as this requires heavy investment on the employers’ part, they have to because cybercrime increases when working remotely.
Remote work does come with added security considerations. Data mishandling and fraud are among them that shape parts of a business’s cybersecurity strategy. Hence, comprehensive remote work policies include powerful tools to ensure customer, company, and employee data integrity.
Establish Cybersecurity Policies
 Policies must be in place in a corporate setting. The same applies to cybersecurity practices. Cybersecurity policies ensure all employees know data security and what they need to do. Do not assume that all employees are affluent with everything regarding cybersecurity.
Policies must be in place in a corporate setting. The same applies to cybersecurity practices. Cybersecurity policies ensure all employees know data security and what they need to do. Do not assume that all employees are affluent with everything regarding cybersecurity.
Hence, draft and establish the relevant cybersecurity policies. Include all security aspects that impact the organization; this includes security protocols, the execution and enforcement, and last but not least, the objective behind them. Also, have a separate security policy to address remote work concerns.
All employees must read, understand and sign off on the policies; they must be responsible and accountable for protecting the company’s data.
Use a Secure Browser
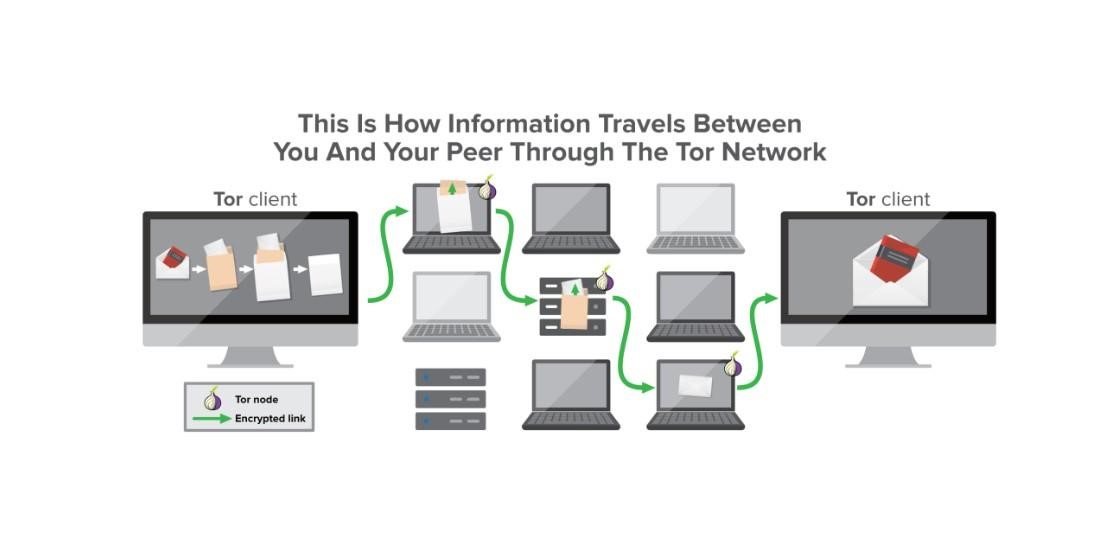
Your browser choice can help keep your data safe. Use a secure browser such as Tor Browser. Tor is aka ‘the onion router’, as it protects your data through multiple layers of encryption like an onion. Tor connects you via its Tor network, where your traffic is randomly routed through a series of servers (nodes/relays); this gives you a high degree of anonymity.
Hence, all your traffic is encrypted. It is almost impossible to trace back to you and for anyone to track what you’re doing online. Anyone trawling you would give up and leave for other easier-to-infiltrate devices.
Many secure browsers will also ensure to force your connections through SSL cert, further safeguarding your data.
Secure Home Routers
 Each employee’s home will have a router, the gateway that allows to and fro communications with the internet. Hackers love to exploit the vulnerabilities that are apparent in wireless routers. Once in, the cybercriminal can do anything, which includes identity theft, data theft, and malware insertions. As such, you must secure this device.
Each employee’s home will have a router, the gateway that allows to and fro communications with the internet. Hackers love to exploit the vulnerabilities that are apparent in wireless routers. Once in, the cybercriminal can do anything, which includes identity theft, data theft, and malware insertions. As such, you must secure this device.
Change the router’s default ID to a unique and complex name that is hard to crack hackers. Remember to use a complicated admin password and regularly change it. Also, update the router’s firmware. These are among the many things you can do to safeguard the home router.
It’s vital to note that home WiFi routers come in many different brands and capabilities. Familiarizing yourself with some notable features can help you pick one with the necessary security and functionality.
Restrict Employee Access
Not all employees need access to all applications across the board in the company. The less handling of a set of data, the fewer the risks. The goal is to reduce data exposure. Hence, restricting employee access is necessary to ensure good data governance and mitigate risks.
 Companies can deploy a secured remote access platform where only authorized users can access specific files, folders, and applications. Just create separate user groups and grant access to the relevant ones.
Companies can deploy a secured remote access platform where only authorized users can access specific files, folders, and applications. Just create separate user groups and grant access to the relevant ones.
Additionally, the IT team can configure the browsers or install a content filter to restrict internet usage. The purpose is to prevent accessing a dubious website that can harm the employee’s device with malware.
However, companies need to be mindful not to go overboard when restricting employees’ access; this can backfire and cause employees to feel disgruntled and lose interest.
Use a VPN
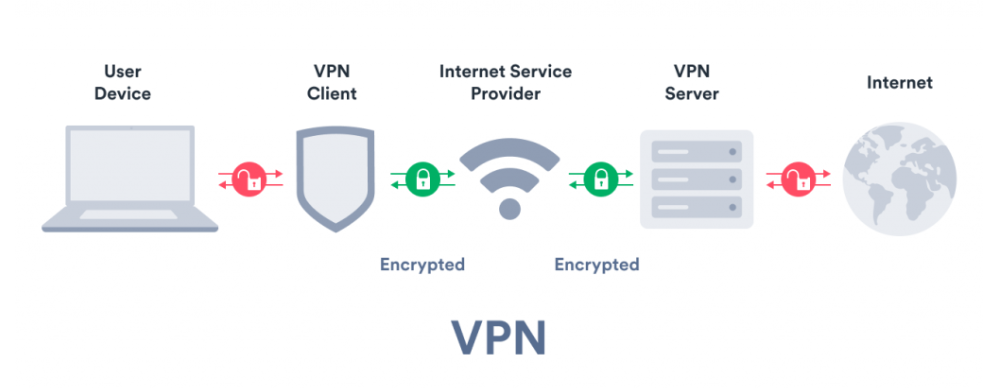 VPN secures internet connections (Source)Securing your home router is one thing but ensuring your internet connections are safe is another. There will be times that you work remotely out of home and connect to unsecured networks; be extra vigilant. Cybercriminals monitor communications in such unsecured networks. Hence, it is dangerous to plug your work devices into these unprotected networks.
VPN secures internet connections (Source)Securing your home router is one thing but ensuring your internet connections are safe is another. There will be times that you work remotely out of home and connect to unsecured networks; be extra vigilant. Cybercriminals monitor communications in such unsecured networks. Hence, it is dangerous to plug your work devices into these unprotected networks.
The simple solution is to use a Virtual Private Network (VPN). A VPN is an essential tool when online, be it anywhere. It encrypts your data in transit, creating a secure connection between your device and the internet. As a result, this protects your data from prying eyes. Also, a VPN masks your IP and secures your privacy.
A word of caution, not all VPNs are the same. Hence, verify the VPN before using it. It is best if the company has done the necessary due diligence and mandated a VPN for all employees.
Use a Password Manager
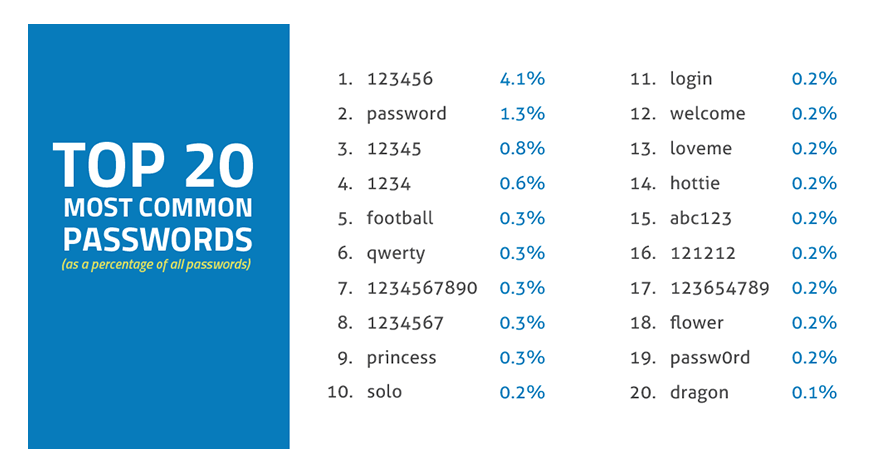
Hackers love to carry out brute force attacks to guess the password to gain access to accounts and steal sensitive information. If you usually use simple or easily guessed passwords, you have to stop and take immediate corrective action.
 Remember, using complicated passwords is key to safeguarding your data:
Remember, using complicated passwords is key to safeguarding your data:
- Minimum 12 characters
- Include uppercase and lowercase letters
- Include letters and numbers
- Include special symbols
Regularly change your passwords, and do not use the same one again. You may feel frustrated with keeping track of so many different and complicated passwords. Fret not and use a password manager.
A password manager is a tool that helps you manage your passwords. It usually comes with a password generator and safely keeps all your passwords in encrypted form. Hence, you won’t have to concern yourself with your passwords.
 Let your password managers do the work for you. Life becomes easier as you remember only the master password that unlocks your password vault. Your password manager automatically logins for you. Also, do not allow your devices to ‘remember’ your passwords; you can set yourself up for a fall if you do.
Let your password managers do the work for you. Life becomes easier as you remember only the master password that unlocks your password vault. Your password manager automatically logins for you. Also, do not allow your devices to ‘remember’ your passwords; you can set yourself up for a fall if you do.
Enable Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) creates an additional security layer to the existing username and password. Two-Factor Authentication (2FA) is a form of MFA and is recommended for all remote workers. The employee has to input the username and password. The employee will then need to provide another piece of information.
In the case of 2FA, a One-Time Password (OTP) reaches the phone. The login requires this OTP to allow access. Since the hacker does not possess the phone, the hacker’s attempt fails. Enabling 2FA helps when a password is compromised. There are other authentication methods, but OTP is common.
Use Anti-Malware Software
 Anti-malware software is a must on all your devices. There is no such thing as trusting the goodwill of anyone to secure your information. Common cybersecurity attacks such as phishing, and infecting with malware or ransomware can easily cause a regrettable data breach.
Anti-malware software is a must on all your devices. There is no such thing as trusting the goodwill of anyone to secure your information. Common cybersecurity attacks such as phishing, and infecting with malware or ransomware can easily cause a regrettable data breach.
Hence, your anti-malware must always run in the background to safeguard your devices from viruses and malicious programs that prey on you. The rule of thumb is never to turn on your devices without an anti-malware program running. However, you should not worry if you use work devices. Ensure the anti-malware software is active.
Use Secure Email
Many communication apps are available in the market, but emails remain the preferred primary form of digital communication worldwide. Hence, it is no wonder that hackers target emails. Malware and phishing are some of the attack modes sent through emails. As such, secure your emails as it protects your company’s data when working remotely.
 For most of you, your IT team would have provided a secure email facility at home. If not, you can look into several secure email services like Atomic Mail that give you the security and privacy you need. Of course, you need end-to-end encryption, and find out the provider’s security policies, features, and others.
For most of you, your IT team would have provided a secure email facility at home. If not, you can look into several secure email services like Atomic Mail that give you the security and privacy you need. Of course, you need end-to-end encryption, and find out the provider’s security policies, features, and others.
ProtonMail is a worthy consideration. It is an open-source and end-to-end encrypted email platform. ProtonMail takes pride in the principle of zero knowledge and zero access; this means that everyone and the email servers cannot access your emails.
Use Encrypted Messaging App
It is common to communicate via messaging apps. Remote workers have a higher need to collaborate through these messaging apps. However, not all messaging apps are created equal, and you cannot afford to be careless with security.
To ensure all your conversations are secure, use encrypted messaging apps like Signal, WhatsApp, or Telegram. The best thing is that they are all free and provide messaging encryption on popular platforms. So, if a nefarious user intercepts your messages, they are unreadable.
Regularly Attend Routine Cybersecurity Training
 Thanks to technological advancement, hacking has evolved with time to become more sophisticated and difficult to counter. Also, human error is one of the leading causes of data security breaches. Hence, your employees must know the latest cybersecurity trends and needs.
Thanks to technological advancement, hacking has evolved with time to become more sophisticated and difficult to counter. Also, human error is one of the leading causes of data security breaches. Hence, your employees must know the latest cybersecurity trends and needs.
Ignorance is not bliss when it comes to cybersecurity. A data security breach can cost an organization everything. Employees are the first line of defense against any potential attack. Hence, companies must train and educate them on how to stay safe online.
Regularly educating the employees also ensures everyone is in sync when safeguarding the company’s data. Hence, companies should be proactive and conduct regular security awareness sessions. Updating the employees on the changing security landscape keeps them informed to mitigate human exposure risks to security threats.
Also read:
- What Are Computer Worms And How to Stop Them?
- Why Integrate Your Web Store with Your ERP System?
- Application support: a necessity or a waste of money?
Wrapping Up
The upward trend in the number of remote work employees is undeniable. However, remote work comes with its challenges, and at the top of them are security risks. Businesses and employees must stress security. Everyone must understand the importance and ways to keep data safe, especially outside their business’ secure network.
The list above will help address remote work security concerns. Take note that this list is not exhaustive. However, they are effective ways to help secure your data and reduce data exposure risks when working remotely.
Thank you!
Join us on social networks!
See you!






