Hello!
Cybersecurity in the current threat landscape is relentless and continuously evolving. Today, it’s up to IT teams to stay a step ahead of hackers. This approach is necessary to effectively defend against increasingly sophisticated attacks.
According to Verizon’s 2020 Data Breach Investigations Report, 71% of data breaches were financially motivated while another 25% were driven by espionage. So it’s same to assume that defending against different evolving strategies and attack vectors isn’t straightforward.
The COVID-19 work from home initiatives, for example, increased enterprise exposure to risk, exponentially. The rush to move up the cloud potentially created many vulnerabilities, and bad actors need to penetrate only one to gain access to enterprise networks.
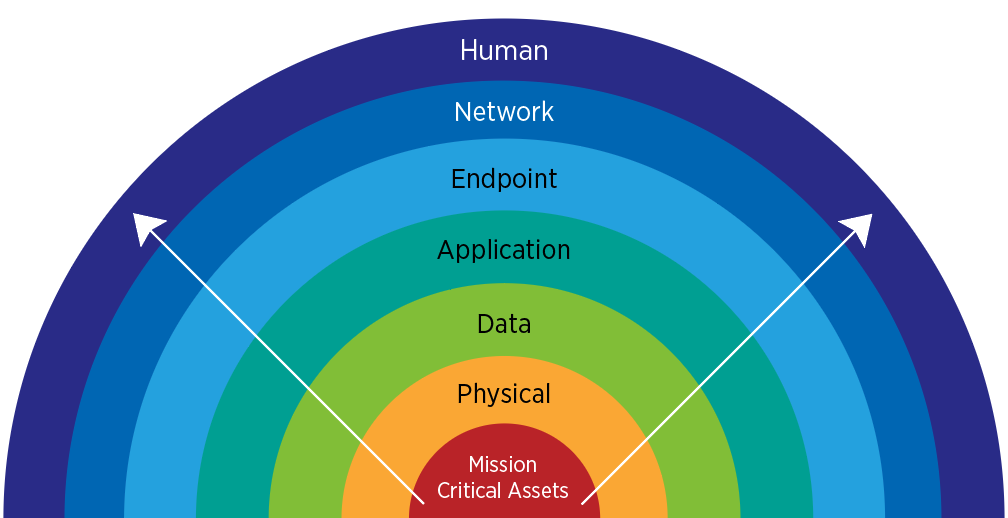
 There are different types of cyber threats, but they all fall into three distinct categories as follows:
There are different types of cyber threats, but they all fall into three distinct categories as follows:
- Attacks on confidentiality (to steal personally identifiable information, trade secrets, or highly classified government data)
- Attacks on integrity (to publicly expose stolen data)
- Attacks on availability (to block access to user data through ransomware attacks)
As there’s no single defense mechanism to ensure robust security, IT and security teams must take a layered approach to secure modern distributed networks. This approach helps security teams continuously update their defenses, beef up IoT networks, guard against mobile malware, botnet attacks, crypto-jacking, etc.
What’s a Layered Approach to Cybersecurity?
 Taking a layered approach to cybersecurity means that IT teams also include all stakeholders, not just technology. This is because you can’t just deploy a web application firewall or some other technology and forget about it anymore.
Taking a layered approach to cybersecurity means that IT teams also include all stakeholders, not just technology. This is because you can’t just deploy a web application firewall or some other technology and forget about it anymore.
The security tools and solutions do form the foundation of a layered security approach. But for robust and effective cybersecurity, you also have to think about people, processes, and the tools involved.
A layered approach combines overlapping security strategies and tools into an integrated framework with people and processes in the mix. This security model helps enhance defenses while mitigating risk.
Why Are People Important?
Humans are the weakest link in your security strategy. According to the Ponemon Institute and IBM’s 2019 Cost of a Data Breach Report, the average cost of a data breach caused by human error is a whopping $3.5 million.
 When staff aren’t aware of security threats, they often create some of the most significant risks. That’s why threat actors specifically target employees counting on their lack of knowledge or inability to follow security best practices.
When staff aren’t aware of security threats, they often create some of the most significant risks. That’s why threat actors specifically target employees counting on their lack of knowledge or inability to follow security best practices.
It’s the primary reason why phishing emails still pose a significant risk to organizations across industries. During the pandemic, the risk of target employees clicking phishing emails with malicious links grew significantly.
So organizations had to engage in regular (remote) training sessions to reaffirm security best practices and make sure employees are aware of potential security threats.
Regular training workshops (online or offline) help build a robust security culture within the organization and keeps security at the forefront. So if there’s a social engineering threat, for example, your staff will be alert to it.
Training is Critical to Staying Alert
Everyone in the company should be trained to follow security best practices from the board-level down to interns.
 These include the following:
These include the following:
- How to spot phishing scams
- Immediately report unusual behavior
- Not opening or clicking links from unknown senders
- Keeping personal and work devices separate (and not using company laptops and mobile devices for personal use)
- Always creating unique and strong passwords (and not reusing them)
- Leveraging two-factor authentication (whenever possible)
- Update and patch all applications, operating systems, and software upon release
- Not installing unknown or unvetted software
- Always connect to enterprise networks via a VPN
Even if your organization has a strong cybersecurity culture, IT teams must leverage access management policies. The best approach here is to follow the least privilege principle based on an employee’s current job and project responsibilities.
What about the Processes?
 The processes involved are essentially the strategies in place to proactively prevent and respond to a security event.
The processes involved are essentially the strategies in place to proactively prevent and respond to a security event.
This means an effective data breach response plan covering repeatable procedures to recover business processes quickly while minimizing the overall damage.
People within the company must also be trained and assigned responsibility to act during an active incident quickly. However, to get this right, it’s vital to hire the right cybersecurity experts for your business and industry niche. This also means that security teams should actively leverage both local and global threat data to better understand the current threat landscape.
What about Security Technologies?
When you have the right security experts on your team, every proactive security strategy will be supported by technologies that best detect and respond to present threats effectively.
There are a wide array of security technologies that are deployed in each layer of your defense posture. The right tool will depend on its ability to facilitate the rapid detection and mitigation of threats while seamlessly integrated into enterprise architecture.
For example, using a VPN or Virtual Private Network is critical when connecting remotely to enterprise networks. This is because VPNs help encrypt all internet traffic, so even if your home network is compromised, your data will be safe from the prying eyes of hackers.
 Some of the best VPNs in 2022 are as follows:
Some of the best VPNs in 2022 are as follows:
- ExpressVPN
- Surfshark
- NordVPN
- IPVanish
- CyberGhost
Different tools and technologies in your IT infrastructure, are segmented (into subnetworks with varying degrees of security), automated with smart algorithms, and leverage deception technologies. The latter will help security specialists deploy dynamic decoys to make life difficult for cybercriminals.
Finally, in the event of a data breach, all of the above will do little to help without robust database encryption technologies. Encryption is like an insurance plan that renders stolen data meaningless without the appropriate decryption keys.
Again, there are plenty of options.
 Some of the best encryption software available in the marketplace is as follows:
Some of the best encryption software available in the marketplace is as follows:
- Folder Lock
- AxCrypt
- CryptoExpert
- CertainSafe
- VeraCrypt
Fortifying enterprise infrastructure demands a layered approach. A perfect balance between people, processes, and technologies lead to a bettered secured future.
Thank you!
Join us on social networks!
See you!